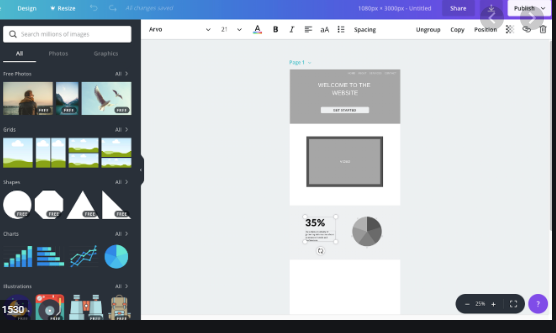
A functional specification is a summary of how the application will function from the customer’s standpoint. The focus of this piece is to describe and analyze a couple of approaches for generating UI mockups. or you can just visit software wireframe wherein you are just going to drag and drop interface to create Wireframes for Dashboard, Mockups for any application including websites and mobile apps.

I am sure that there are numerous unique procedures for creating wireframes. Still, I am only able to describe and comment on people I have used, making some general announcements about what is excellent (or bad) concerning them.
Lo-Fi Prototyping
This is the fancy name because of its previous butcher’s paper plan. Slimming down is the perfect technique when a brand-new shrink-wrapped software bundle was designed.I once spent four days with a group of developers in a small apartment designing a telecommunications application using this technique. The result was short of astounding; it allowed us to blast out and iterate ideas quickly. As the team’s UI designer, I went home at the end of the week with a mass of paper, which I turned into over 30 HTML mockups.
This approach is unsuitable for designing simple business websites or software which has been done before (e.g., non-novel systems like a shopping cart). It’s also not so great when a client is directly involved in the project. There are a few reasons for this; it requires a big investment of time on the client’s behalf (they may have a business to run during the day), and secondly; the client-to-supplier relationship often creates a dynamic where they tell you what they want, and you go off and make it. Usually, the client won’t hang around while you design their software.
Microsoft Excel
Yes, as strange as it may sound, MS Excel can be quite handy for producing wireframes, especially for software that is expected to have long vertically scrolling screens. I would never have thought to use it myself, but a company I worked for introduced me to it as their preferred specific tool.First, I was skeptical, but I quickly warmed to the approach when I saw how fast screens were to make once I got the hang of it. It’s excellent for inserting instructions to programmers (either in comments or as sidebar text). However, it produces exceedingly ugly wireframes; this is a good thing for application design since it keeps everyone’s focus on usability and business logic.
The other great thing about Excel is everyone is familiar with it, including clients. The closest thing I could think of as a criticism of Excel as a wireframe tool is that it produces decidedly uninspiring visuals. I currently don’t use Excel as a wireframe tool, but I would have no problem picking it up again if I felt it was right for a project.
Microsoft Word
Another desktop application you wouldn’t usually think of as a wireframe tool, Word can be pretty good in certain situations. Generally, the only time I would use Word to represent UI controls is to make a ‘mini-spec’ for a web-based application.
A mini-spec is created in one of two situations; as an adjunct to an already ratified functional specification, or as a mechanism for grouping together a bunch of features for a version upgrade. UI controls are represented in a rudimentary fashion, for instance; (*) would be a radio button, and [x] would be a checkbox, etc.This works because the system’s interface has already been established (i.e., the order has been coded, or a Photoshop mockup exists).
The advantage of this approach is speed; you describe the underlying functionality of the code and only mockup the controls relevant to the feature instead then drawing the entire screen.Over the past few years, I have been exposed to several techniques for preparing mockups. Each approach has its strengths and weaknesses, but generally, the best method to use depends on the project at hand. I don’t have a single preferred plan, but choosing the most appropriate style to use at the time can be a tricky undertaking.
HTML Mockups
With the advent of such as like Microsoft FrontPage and its successor Web Expression, anyone can make cool looking mockups, to the point where it seemed as though all that was left to do was hand over the HTML to the programmers, and they would take care of the rest.
I’ve used FrontPage to make HTML mockups quite a bit in the past. Some analysts say it’s a reliable option for designs because it allows you to produce navigable HTML. From my experience, I don’t think it’s an excellent choice to use as a first draft system.
It can be time-consuming and lures you to distraction by unnecessary detail early on (i.e., making the design’s look pretty’).The biggest problem with HTML mockups is you have nowhere to put annotations (i.e., generally tech notes directed at programmers describing ‘under the hood’ functionality). As far as navigable mockups go, I’ve never found it to be a big issue with flat mockup structures. Generally, people know where pages are going to go to, and in rare cases, when a page is going to the wrong place, its nearly always an essential task to direct it elsewhere.
There is one instance when an HTML mockup is appropriate straight away. This is when a sophisticated new screen is being added to an already established interface. The reasons for this are beyond the scope of this article, but suffice it to say that experience has shown that it’s quicker than first creating a lo-fi version of the UI. One of the other great things about HTML mockups is that they’re easy to distribute to people.
Microsoft Visio
this is the tool I use at the moment for wireframes. It strikes the right balance between flexibility, professionalism, and speed. Visio is great for putting in tech notes without interfering with the wireframe itself; I generally put these in a sidebar to the right.
Visio interfaces come out looking beautiful, and every day, which is what you want. It also has drop-in vector art for all the most common form controls you need (e.g., text boxes, radio buttons, etc.).I find that Visio is well suited for use with clients and their custom web applications. The only fault I can find with Visio is it’s hard to distribute files, few people have Visio installed on their computers (especially clients), but this is easy to get around, I print wireframes to PDF.
Photoshop
Mainly used by graphic designers to create compelling visual layouts. The beauty of Photoshop is realism. This can be quite exciting since it creates a real buzz on a project, as though things are starting to shift from concept to reality.Photoshop is best used for creating a single, highly polished UI screen. For example, just the home page of a business website, or only the landing page of a web-based application. I have seen graphic designers produce every expected screen of a business website in Photoshop; this is unnecessary.
The client will get what their website is going to look like from just the home page (i.e., it establishes what the overall look and feel of the site will be).The obvious shortcoming of employing Photoshop is the skill required to use the program; it often takes years just to become proficient with the tool. Iterations can often be slower than other techniques, especially when a sophisticated design with many layers is involved. On the plus side, distribution is a breeze since Photoshop can save image files which anyone can open (e.g., JPEG or PNG).One of the perils of making wireframes that are seen by a client is the tendency to get distracted by cosmetic factors (e.g., client: “why is everything grey?”, “can we have that button in green?”, “that’s not our logo!”).
Generally, what I do before designing anything is to tell the client, “I’m going to make some very rough mockups of how the screens will look. It won’t be pretty, but we are trying to lock-down where buttons go, the general layout, etc.”.This is where methods like lo-fi prototyping or MS Excel can be helpful because the screens can’t help but look hideous. The danger with mockups in HTML or Photoshop is that effort can be spent early on ‘making it pretty.’ The problem with making things ‘look pretty’ at early stages is time gets wasted when iterative adjustments occur (which they will).Iterations are the name of the game when designing a system, especially early on. If this is the case, then you want to choose the approach that will allow you to churn out revisions at super-high speeds.

 You do not need to operate at 3%, but your internet customers are maybe surfing the internet at any moment. It makes sense to make a website that’s available for your clients and you 365 days per year, 24/7, does not it?
You do not need to operate at 3%, but your internet customers are maybe surfing the internet at any moment. It makes sense to make a website that’s available for your clients and you 365 days per year, 24/7, does not it?




 Basics of Vape Pens
Basics of Vape Pens You can use your vape pen to consume, CBD oils or marijuana, and tobacco concentrate. In many cases, the concentrates contain high levels of the main ingredient giving you a perfect hit. This also allows you to get high within a short period if, for instance, you were vaping marijuana.
You can use your vape pen to consume, CBD oils or marijuana, and tobacco concentrate. In many cases, the concentrates contain high levels of the main ingredient giving you a perfect hit. This also allows you to get high within a short period if, for instance, you were vaping marijuana.










 prepared to assist nurses and provide medical and nursing care.
prepared to assist nurses and provide medical and nursing care.
 It is critical to note that one of the significant bonuses you will get from carry-on bags is that all of your items are with you at all times. Therefore, you will not face any potential delay with your luggage.
It is critical to note that one of the significant bonuses you will get from carry-on bags is that all of your items are with you at all times. Therefore, you will not face any potential delay with your luggage.



 After you have come up with an app, you will need an application developer to assess the app and come with feature the will make the app better. One professional service that the company will get from the application developer is application assessment. The mobile app will be more polished, and the platform will be more accepted by the users.
After you have come up with an app, you will need an application developer to assess the app and come with feature the will make the app better. One professional service that the company will get from the application developer is application assessment. The mobile app will be more polished, and the platform will be more accepted by the users. The mobile has gone through all the stages required. The mobile app developer will test if the app is working properly before presenting it to the public.
The mobile has gone through all the stages required. The mobile app developer will test if the app is working properly before presenting it to the public. Much of the socialization of the modern youth takes place in the cyberspace. Many credible surveys have revealed that the average youth spends close to two-thirds of their time on the internet. Youthful socialization takes place on Facebook or Twitter. This reality limits the teenagers’ capacity for healthy interpersonal relationships.
Much of the socialization of the modern youth takes place in the cyberspace. Many credible surveys have revealed that the average youth spends close to two-thirds of their time on the internet. Youthful socialization takes place on Facebook or Twitter. This reality limits the teenagers’ capacity for healthy interpersonal relationships. As a result, many teenagers are likely to be misinformed about many important issues that connect with their lives. This implies that technology is likely to ruin the perceptions of the youth about values, morality, and virtue. That is why many youths have been convinced to join the ranks of extremist groups and subversive secret societies.
As a result, many teenagers are likely to be misinformed about many important issues that connect with their lives. This implies that technology is likely to ruin the perceptions of the youth about values, morality, and virtue. That is why many youths have been convinced to join the ranks of extremist groups and subversive secret societies.
 Healthcare IT technology can be positively implemented in nine specialized areas of hospital management. The first of these is the electronic health record keeping. Here, an electronic cabinet is created for every patient and all information, including images, healthcare records and notes are stored safely. This would greatly assist in providing quality service to patients since easy tracking of patients and retrieval of patient data are possible.
Healthcare IT technology can be positively implemented in nine specialized areas of hospital management. The first of these is the electronic health record keeping. Here, an electronic cabinet is created for every patient and all information, including images, healthcare records and notes are stored safely. This would greatly assist in providing quality service to patients since easy tracking of patients and retrieval of patient data are possible. Automated dispensing machines, electronic material management, interoperability between different organizations or hospitals, bar coding of healthcare environment are the remaining fields where IT can aid immensely. In short, incorporating the ever-improving healthcare IT technology in the day-to-day functioning of a hospital can greatly improve the efficiency of the healthcare staff as well as the supporting staff, enhance the comforts of the patient, make clinical operations easier and faster and thus improve the overall ambience of a hospital. After all, healthcare means putting the patients to ease and curing them, this increases survival rates.
Automated dispensing machines, electronic material management, interoperability between different organizations or hospitals, bar coding of healthcare environment are the remaining fields where IT can aid immensely. In short, incorporating the ever-improving healthcare IT technology in the day-to-day functioning of a hospital can greatly improve the efficiency of the healthcare staff as well as the supporting staff, enhance the comforts of the patient, make clinical operations easier and faster and thus improve the overall ambience of a hospital. After all, healthcare means putting the patients to ease and curing them, this increases survival rates.